Smaller cipher text compares to original plain text file. Symmetric encryption is much faster to execute because of its shorter key lengths.

Symmetric Vs Asymmetric Encryption Difference Explained
It evokes a sense of modernism and movement.
. Symmetrical balance on the other hand is when you have two identical sides of a design with. First week only 499. Symmetric encryption is a simple technique compared to asymmetric encryption as only one key is employed to carry out both the operations.
Tasks of the operating system are done by master processor. Asymmetrical balance is when you have two dissimilar sides of a design and have positioned visual weight unequally and yet youve still achieved a sense of balance. For example 603 means 60 Mbps.
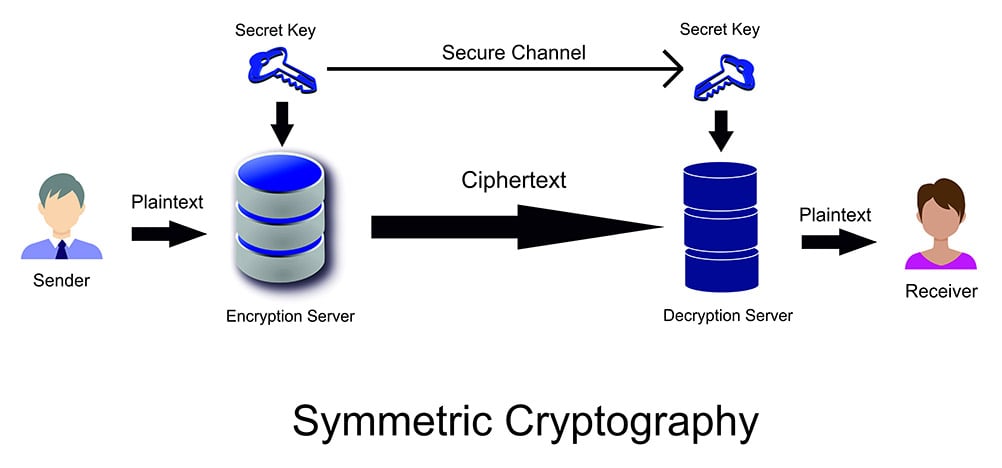
A connection with equal download and upload speeds. Irregular in shape or outline. We use symmetric key encryption when we need to transfer large chunks of information and data.
Asymmetrical balance is more dynamic and interesting. Symmetric key encryption works on low usage of resources. Exhibiting equivalence or.
Having a common measure. Asymmetry on the other hand refers to anything that isnt symmetrical. The question though was about asymmetric balance.
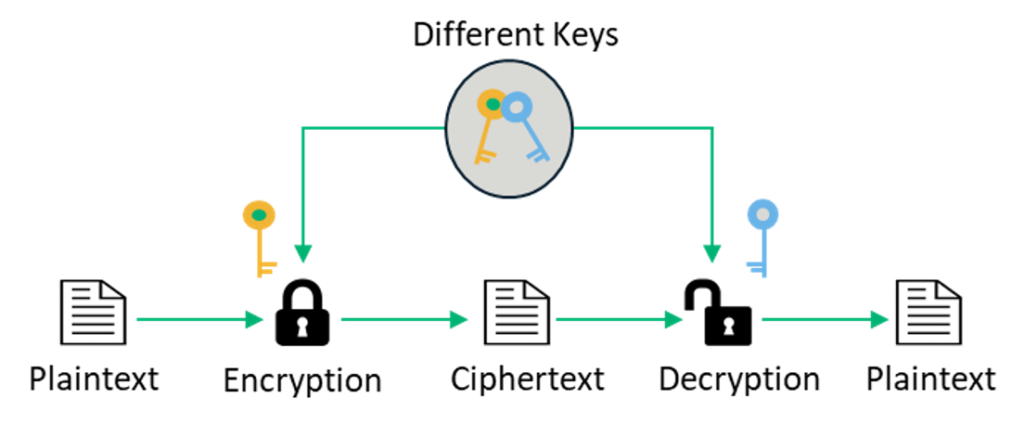
An asymmetrical connection however does NOT have equal downloadupload speeds. Using any particular definition of what symmetry and asymmetry are its easy to point to the difference since theres a hard line between the two. Asymmetric Encryption consists of two cryptographic keys.
Symmetric Vs Asymmetric - 15 images - ppt cryptography basics powerpoint presentation id 4023298 the complete cryptography guide asymmetric vs symmetric ppt intrauterine growth restriction powerpoint symmetry special issue symmetry and asymmetry. A dress with an crooked hemline. Obviously r 1.
In asymmetric multiprocessing the processors are not treated equally. Write Python code Using turtle graphics this shape. But asymmetric has multiple applications.
Larger cipher text compares to original plain text file. Start your trial now. These keys are regarded as Public Key and Private Key.
In the case of a logo if theres any difference between the left and right halves its asymmetric to one degree or another. These are the tradeoffs worth considering when deciding which type of encryption to employ. The g q Nandn F 0 BNq.
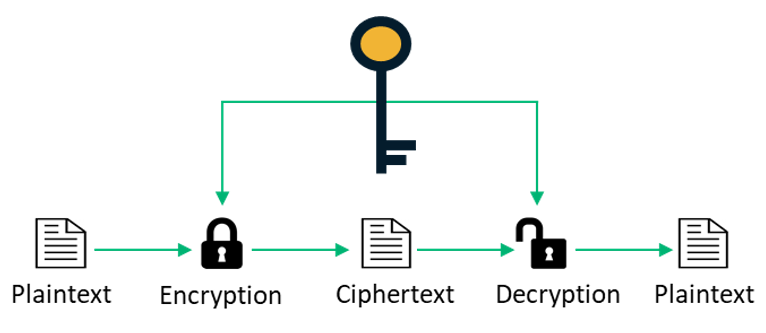
Asymmetric key key uses different keys. It only requires a single key for both encryption and decryption. In symmetric multiprocessing all the processors are treated equally.
Symmetry is the visual quality of repeating parts of an image across an axis along a path or around a center. Asymmetric encryption has a tendency to bog down networks because of its longer key lengths and complex algorithms. The size of cipher text is same or smaller than the original plain text.
Having similarity in size shape and relative position of corresponding parts. Symmetric encryption incorporates only one key for encryption as well as decryption. We write N nn-12 and Bhk hlkh-k.
The encryption process in asymmetric encryption is slower as it uses two different keys. Size of cipher text. Hence symmetric encryption requires a priori key exchange.
Tasks of the operating system are done individual processor. Solution for what is the difference between symmetric and asymmetric. It evokes feelings of modernism movement energy and vitality.
Balance is the visual principle of making a design appear equally weighted throughout the composition. This is why we use larger keys in asymmetric encryption. The encryption process of symmetric encryption is faster as it uses a single key for encryption and decryption.
It is much faster and provides confidentiality for large chunks of data. Both keys are related to each other through the complicated mathematical process. It requires two key one to encrypt and the other one to decrypt.
Symmetrical connections are exactly what they sound like. In whatever schemes known so far symmetric encryption is lot faster than asymmetric. We say that an unlabelled grap ish symmetric or asymmetric according as the graph obtained by labelling its nodes is symmetric or asymmetric.
Thats because in asymmetric encryption that uses smaller keys having the public key actually makes the private key easier to calculate. The size of cipher text is same or larger than the original plain text. Thus this type of balance tends to be more interesting the harmonious expression of symmetrically balanced compositions tend to be somewhat passive while designers using asymmetrically balanced designs usually do not.
Symmetric encryption is more secure than asymmetric encryption when you use smaller key sizes such as a 256-bit key. Since asymmetric-key ie public-key cryptography requires fewer keys overall and symmetric-key cryptography is significantly faster a hybrid approach is often used whereby asymmetric-key algorithms are used for the generation and verification of digital signatures and for initial key establishment while symmetric-key algorithms are used for all other purposes. Symmetric encryption is mainly used to transmit bulk data.
If an nq graph is symmetric of order r then so is its complement ie. Radial balance occurs when elements radiate from a common center. It ensures non-repudiation authenticity added to confidentiality.
Balance measures the visual weight of your composition. Symmetric Key Encryption Asymmetric Key Encryption. For example with a 500500 Mbps fibre internet connection you get 500 Mbps of download AND 500 Mbps of upload speeds.
Explain the key difference between how symmetric encryption works and how asymmetric encryption works. Used to transmit small data. Asymmetric Multiprocessing Symmetric Multiprocessing.
Asymmetrical images attract more attention due to the more complex relationship between objects used to create the composition. In asymmetric key scheme each user has a public and a private secret key. Asymmetrical balance offers more visual variety although it can be more difficult to achieve because the relationships between elements are more complex.
We use asymmetric key encryption when we need to transfer only very small amounts of data. Used to transmit big data.

Symmetric Vs Asymmetric Encryption 5 Differences Explained By Experts
Symmetric Vs Asymmetric Encryption 5 Differences Explained By Experts
0 Comments